|
| 1 | +# Set up HTTPS on a subdomain |
| 2 | + |
| 3 | +_WARNING: you are on the master branch, please refer to the docs on the branch that matches your `cortex version`_ |
| 4 | + |
| 5 | +The recommended way to set up HTTPS with trusted certificates is by using [API Gateway](../api-gateway.md) because it's simpler and enables you to use API Gateway features such as rate limiting (it also supports custom domains). This guide is only recommended if HTTPS is required and you don't wish to use API Gateway (e.g. it doesn't support your use case due to limitations such as the 29 second request timeout). |
| 6 | + |
| 7 | +This guide will demonstrate how to create a dedicated subdomain in AWS Route 53 and use an SSL certificate provisioned by AWS Certificate Manager (ACM) to support HTTPS traffic to Cortex APIs. By the end of this guide, you will have a Cortex cluster with APIs accessible via `https://<your-subdomain>/<api-endpoint>`. |
| 8 | + |
| 9 | +You must own a domain and be able to modify its DNS records. |
| 10 | + |
| 11 | +## Step 1 |
| 12 | + |
| 13 | +Decide on a subdomain that you want to dedicate to Cortex APIs. For example if your domain is `example.com`, a valid subdomain can be `api.example.com`. |
| 14 | + |
| 15 | +This guide will use `cortexlabs.dev` as the example domain and `api.cortexlabs.dev` as the subdomain. |
| 16 | + |
| 17 | +## Step 2 |
| 18 | + |
| 19 | +We will set up a hosted zone on Route 53 to manage the DNS records for the subdomain. Go to the [Route 53 console](https://console.aws.amazon.com/route53/home) and click "Hosted Zones". |
| 20 | + |
| 21 | + |
| 22 | + |
| 23 | +## Step 3 |
| 24 | + |
| 25 | +Click "Create Hosted Zone" and then enter your subdomain as the domain name for your hosted zone and click "Create". |
| 26 | + |
| 27 | + |
| 28 | + |
| 29 | +## Step 4 |
| 30 | + |
| 31 | +Take note of the values in the NS record. |
| 32 | + |
| 33 | + |
| 34 | + |
| 35 | +## Step 5 |
| 36 | + |
| 37 | +Navigate to your root DNS service provider (e.g. Google Domains, AWS Route 53, Go Daddy). Your root DNS service provider is typically the registrar where you purchased your domain (unless you have transferred DNS management elsewhere). The procedure for adding DNS records may vary based on your service provider. |
| 38 | + |
| 39 | +We are going to add an NS (name server) record that specifies that any traffic to your subdomain should use the name servers of your hosted zone in Route 53 for DNS resolution. |
| 40 | + |
| 41 | +`cortexlabs.dev` is managed by Google Domains. The image below is a screenshot for adding a DNS record in Google Domains (your UI may differ based on your DNS service provider). |
| 42 | + |
| 43 | +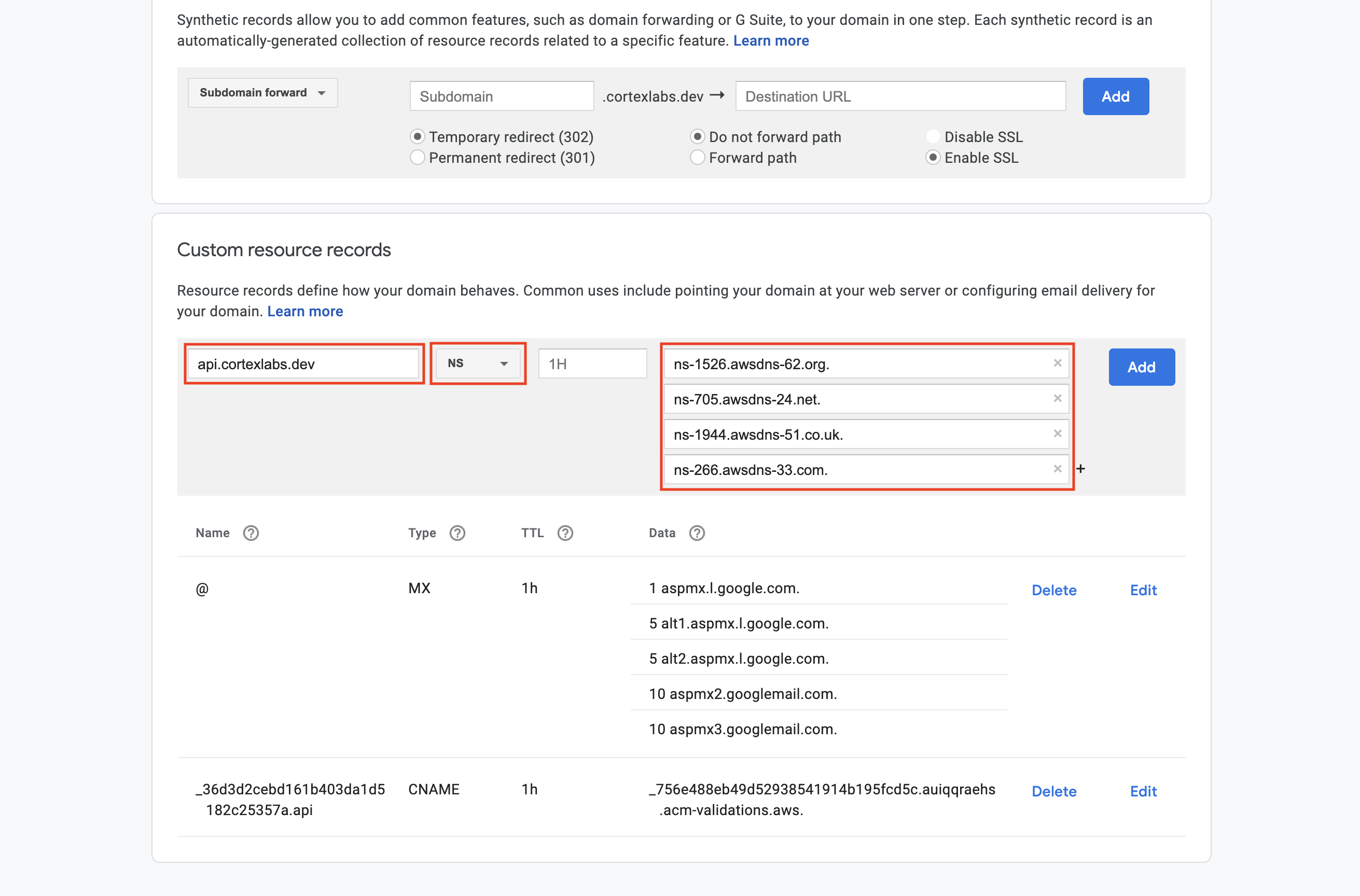 |
| 44 | + |
| 45 | +## Step 6 |
| 46 | + |
| 47 | +We are now going to create an SSL certificate for your subdomain. Go to the [ACM console](https://us-west-2.console.aws.amazon.com/acm/home) and click "Get Started" under the "Provision certificates" section. |
| 48 | + |
| 49 | + |
| 50 | + |
| 51 | +## Step 7 |
| 52 | + |
| 53 | +Select "Request a public certificate" and then "Request a certificate". |
| 54 | + |
| 55 | + |
| 56 | + |
| 57 | +## Step 8 |
| 58 | + |
| 59 | +Enter your subdomain and then click "Next". |
| 60 | + |
| 61 | + |
| 62 | + |
| 63 | +## Step 9 |
| 64 | + |
| 65 | +Select "DNS validation" and then click "Next". |
| 66 | + |
| 67 | + |
| 68 | + |
| 69 | +## Step 10 |
| 70 | + |
| 71 | +Add tags for searchability (optional) then click "Review". |
| 72 | + |
| 73 | + |
| 74 | + |
| 75 | +## Step 11 |
| 76 | + |
| 77 | +Click "Confirm and request". |
| 78 | + |
| 79 | + |
| 80 | + |
| 81 | +## Step 12 |
| 82 | + |
| 83 | +Click "Create record in Route 53". A popup will appear indicating that a Record is going to be added to Route 53. Click "Create" to automatically add the DNS record to your subdomain's hosted zone. Then click "Continue". |
| 84 | + |
| 85 | + |
| 86 | + |
| 87 | +## Step 13 |
| 88 | + |
| 89 | +Wait for the Certificate Status to be "issued". This might take a few minutes. |
| 90 | + |
| 91 | + |
| 92 | + |
| 93 | +## Step 14 |
| 94 | + |
| 95 | +Take note of the certificate's ARN. The certificate is ineligible for renewal because it is currently not being used. It will be eligible for renewal after it is used in Cortex. |
| 96 | + |
| 97 | + |
| 98 | + |
| 99 | +## Step 15 |
| 100 | + |
| 101 | +Add the following field to your cluster configuration: |
| 102 | + |
| 103 | +```yaml |
| 104 | +# cluster.yaml |
| 105 | + |
| 106 | +... |
| 107 | + |
| 108 | +ssl_certificate_arn: <ARN of your certificate> |
| 109 | +``` |
| 110 | +
|
| 111 | +and then create a Cortex cluster. |
| 112 | +
|
| 113 | +```bash |
| 114 | +$ cortex cluster up --config cluster.yaml |
| 115 | +``` |
| 116 | + |
| 117 | +## Step 16 |
| 118 | + |
| 119 | +After your cluster has been created, navigate to your [EC2 Load Balancer console](https://us-west-2.console.aws.amazon.com/ec2/v2/home#LoadBalancers:sort=loadBalancerName) and locate the Cortex API load balancer. You can determine which is the API load balancer by inspecting the `kubernetes.io/service-name` tag. |
| 120 | + |
| 121 | +Take note of the load balancer's name. |
| 122 | + |
| 123 | +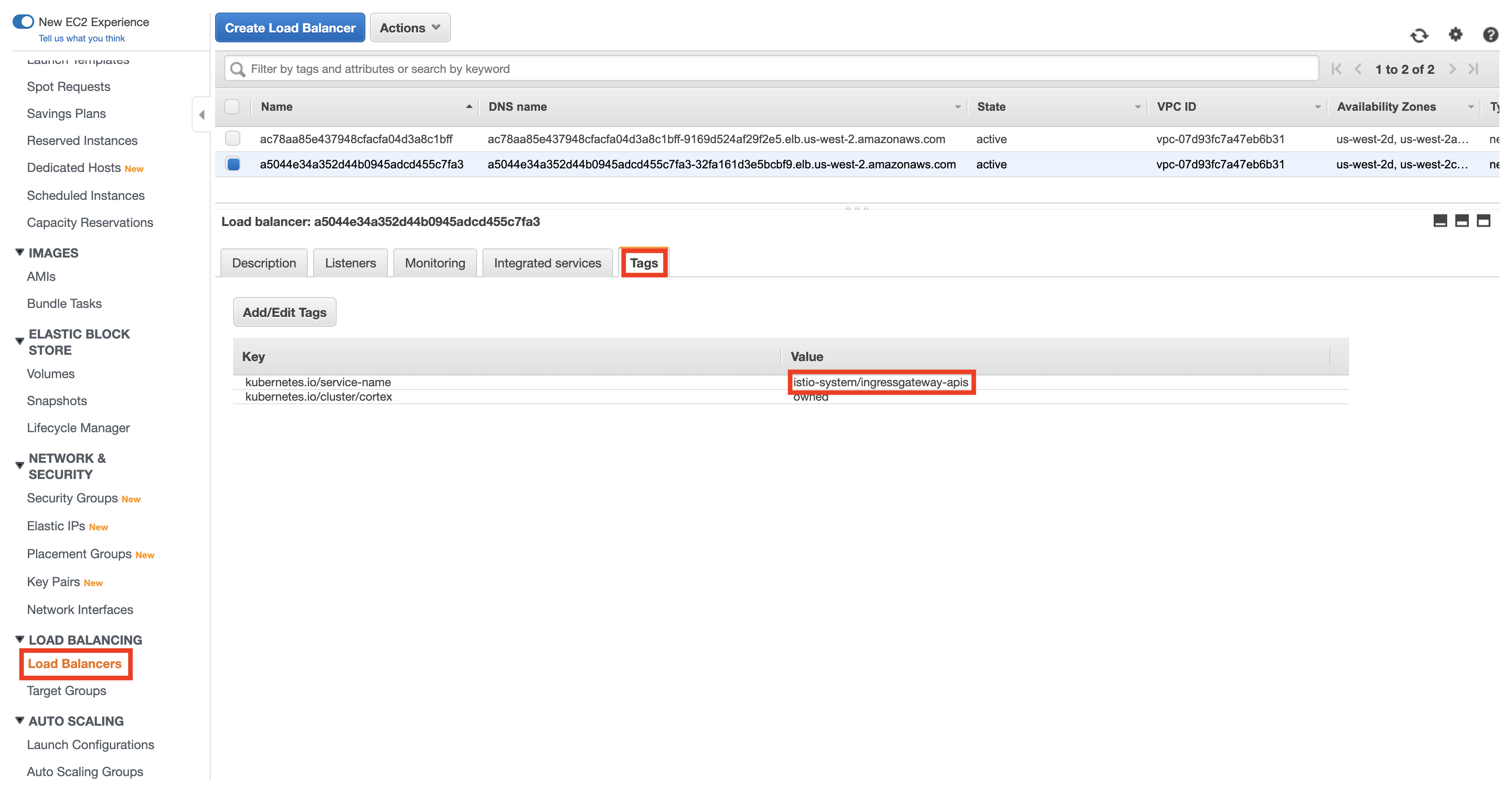 |
| 124 | + |
| 125 | +## Step 17 |
| 126 | + |
| 127 | +Go to the hosted zone you created in the [Route 53 console](https://console.aws.amazon.com/route53/home#hosted-zones:) and add an Alias record that routes traffic to your Cortex cluster's API load balancer (leave "Name" blank). |
| 128 | + |
| 129 | +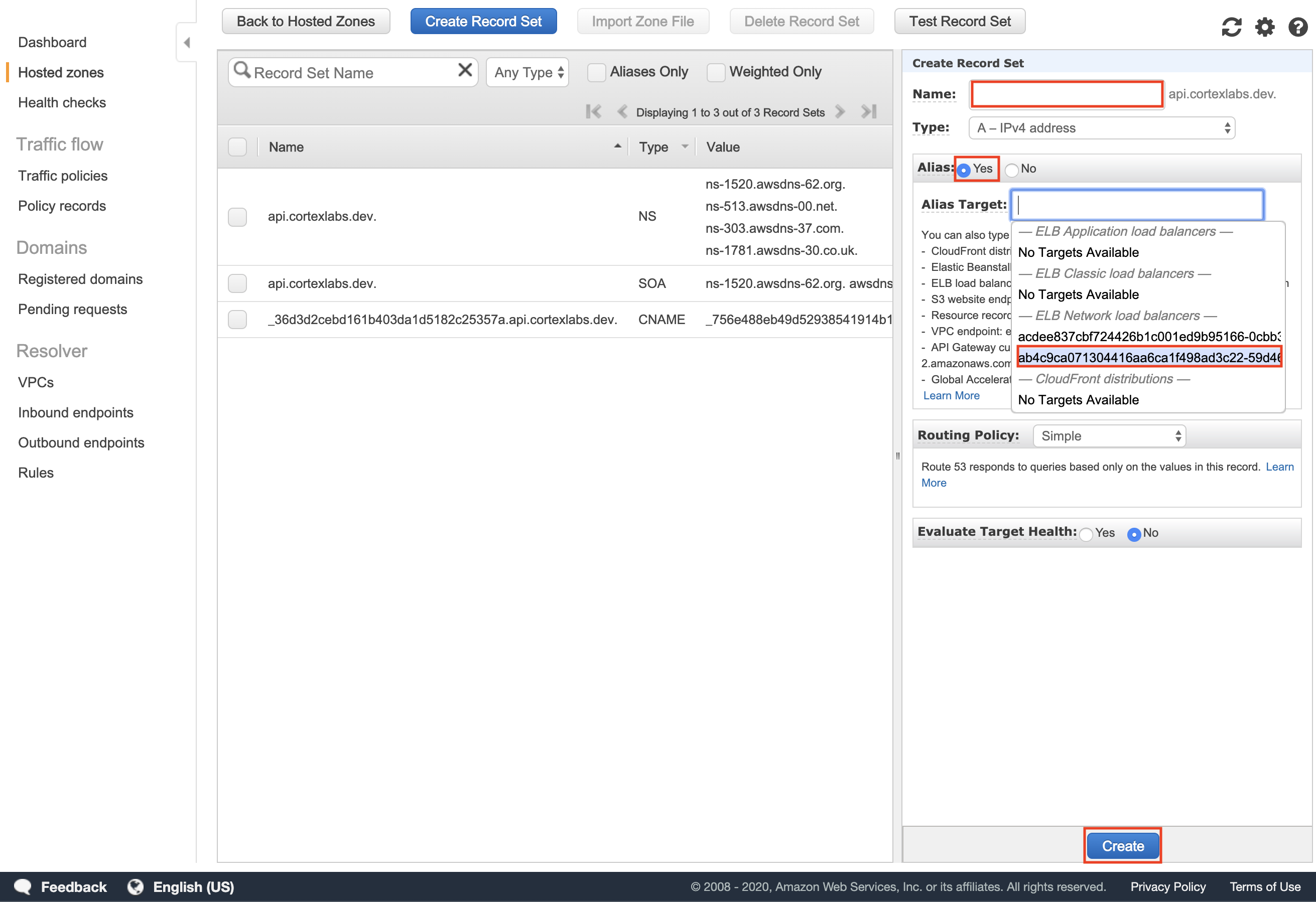 |
| 130 | + |
| 131 | +### Using your new endpoint |
| 132 | + |
| 133 | +You may now use your subdomain in place of your API load balancer endpoint in your client. For example, this curl request: |
| 134 | + |
| 135 | +```bash |
| 136 | +curl http://a5044e34a352d44b0945adcd455c7fa3-32fa161d3e5bcbf9.elb.us-west-2.amazonaws.com/iris-classifier -X POST -H "Content-Type: application/json" -d @sample.json |
| 137 | +``` |
| 138 | + |
| 139 | +Would become: |
| 140 | + |
| 141 | +```bash |
| 142 | +curl https://api.cortexlabs.dev/iris-classifier -X POST -H "Content-Type: application/json" -d @sample.json |
| 143 | +``` |
| 144 | + |
| 145 | +### Cleanup |
| 146 | + |
| 147 | +Spin down your Cortex cluster. |
| 148 | + |
| 149 | +Delete the hosted zone for your subdomain in the [Route 53 console](https://console.aws.amazon.com/route53/home#hosted-zones:): |
| 150 | + |
| 151 | +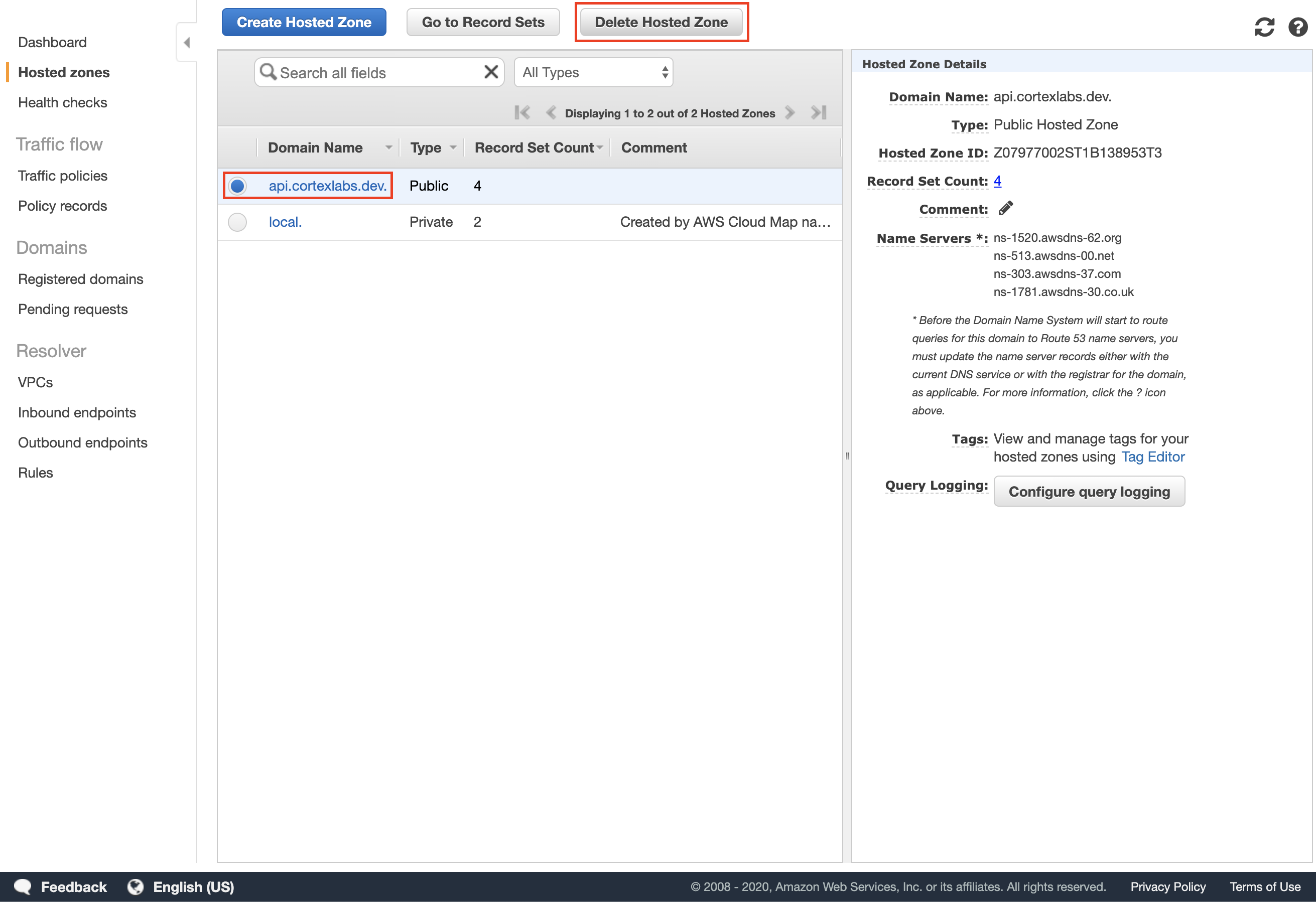 |
| 152 | + |
| 153 | +Delete your certificate from the [ACM console](https://us-west-2.console.aws.amazon.com/acm/home): |
| 154 | + |
| 155 | + |
0 commit comments